Deep Dive: Building a Zero Trust–Powered Security Architecture
- Eric Zhu
- Apr 14, 2025
- 3 min read
Updated: May 8, 2025
In today’s distributed IT landscape, perimeter-only defenses can no longer keep pace with evolving threats and compliance demands. A Zero Trust security model—centered on “never trust, always verify,” least-privilege access, and continuous monitoring—offers a modern blueprint for protecting every user, device, and workload as if it resides in an untrusted network. Layered atop this model, an end-to-end adoption framework guides organizations through staged assessment, prioritization, implementation, and ongoing improvement. The following sections unpack each component and explain why our team’s real-world experience makes this approach exceptionally effective.
1. Adoption Framework: From Assessment to Continuous Improvement
1.1 End-to-End Assessment
Begin with a comprehensive inventory of all users, devices, applications, data stores, and network segments—across on-premises, multi-cloud, and hybrid environments. Map business drivers, regulatory requirements, and top threat scenarios to ensure every risk surface is accounted for.
1.2 Ruthless Prioritization
Analyze gaps against your ideal Zero Trust state and identify “quick wins” that deliver the greatest risk reduction (e.g., enforcing multi-factor authentication on high-privilege accounts, segmenting critical workloads). Tackle these first to build momentum and demonstrate value.
1.3 Continuous Improvement
Establish key metrics—mean time to remediate (MTTR), percentage of assets in compliance, number of unauthorized access attempts blocked—and review them on a regular cadence. Adjust controls, policies, and investments based on real-time threat intelligence and operational feedback.
2. Core Zero Trust Principles
2.1 Assume All Traffic Is Potentially Malicious
No user or device is implicitly trusted, whether inside the corporate network or connecting remotely. Every access request must prove its legitimacy via continuous identity and device validation.
2.2 Enforce Least-Privilege Access
Grant users and services only the minimum rights needed—and only for the duration necessary to complete their tasks. This “just-in-time” and “just-enough” access approach limits lateral movement in the event of credential compromise.
2.3 Continuous Monitoring & Validation
Collect telemetry from all network flows, endpoints, and application logs. Analyze behavior patterns to detect anomalies, then automatically quarantine or escalate for investigation. This forms a closed-loop “detect and respond” system that reduces dwell time and business impact.
3. End-to-End Strategy & Implementation
3.1 Identity & Access Management
Shift access controls from static network boundaries to per-application and per-resource policies. Integrate multi-factor authentication, contextual risk scoring, and adaptive access rules so that every sign-in and request is dynamically evaluated.
3.2 Micro-Segmentation & Network Isolation
Divide network zones and application tiers into granular segments. Enforce policy at each boundary to block unauthorized east-west traffic, and automate responses to suspicious lateral movements.
3.3 Data Protection
Discover, classify, and encrypt sensitive data at rest and in transit. Embed data-centric controls into workflows, ensuring that only authorized processes and users can access critical information.
3.4 Automated Security Operations
Build a unified security operations center that ingests events from across the estate, applies playbooks for routine incident handling, and triggers automated remediation for common threats—freeing analysts to focus on high-impact investigations.
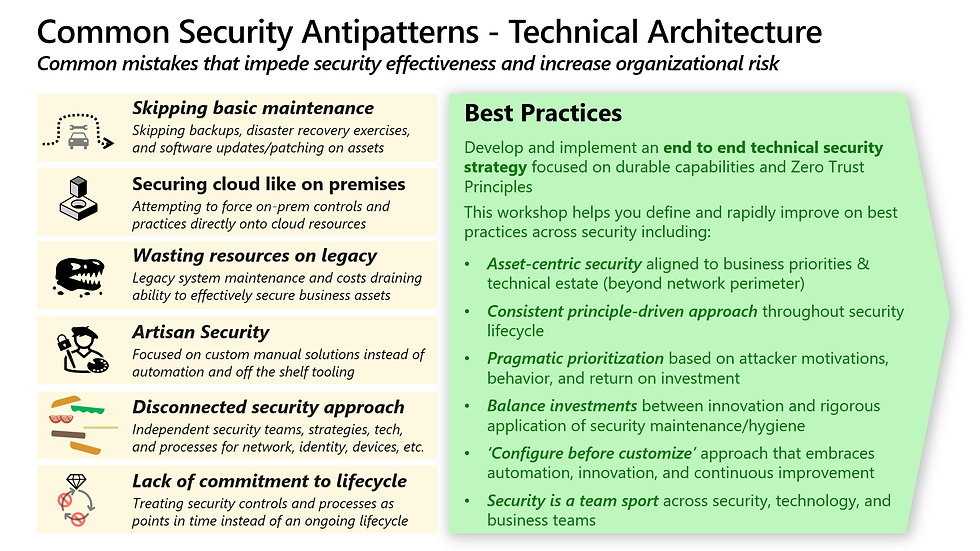
4. Antipatterns & Best Practices
Common Pitfalls
Firewall-Only Mindset: Simply lifting existing perimeter rules into a new environment leaves gaps and blind spots.
Big-Bang Deployments: One-time projects quickly become outdated; security needs an ongoing lifecycle.
Overly Custom Rules: Manual policies don’t scale—automation is key to consistent enforcement.
Recommended Practices
Asset-Centric Focus: Anchor all controls and monitoring around your highest-value assets, not just generic network segments.
Configuration-First Approach: Leverage built-in, automated policies before layering custom scripts—this accelerates deployment and reduces human error.
Balanced Defense & Response: Combine proactive controls (“prevent”) with rapid detection and containment (“respond”) to minimize business disruption.
5. Why Our Team Delivers Real-World Results
Deep Industry Expertise Hands-on leadership of Zero Trust architecture and certification efforts in high-compliance environments (e.g., semiconductor manufacturing) has honed our ability to block advanced threats at scale.
Cross-Domain Compliance Insights We translate regulatory requirements and threat landscapes into tailored Zero Trust roadmaps, ensuring both security and audit readiness.
AI-Driven Security Orchestration Our automated playbooks and advanced analytics accelerate threat detection and response—reducing mean time to detect (MTTD) and MTTR by orders of magnitude.
End-to-End Delivery From executive workshops and strategic planning to technical design, implementation sprints, and continuous maturity assessments, we provide seamless project management and accountability.
By combining a robust adoption framework with the Zero Trust model’s core tenets—continuous verification, least-privilege access, and automated monitoring—you can build a security architecture that not only withstands today’s threats but adapts to tomorrow’s. Ready to transform your security posture? Reach out for a customized assessment and roadmap.



Comments